Cloud & Security Solutions



MICROSOFT 365
seamless collaboration, secure file sharing, and real-time communication across devices. With built-in security, AI-powered insights, and cloud storage, Microsoft 365 helps businesses enhance productivity, streamline workflows, and stay connected anytime, anywhere.

>> OFFICE PRO PLUS
OFFICE APPS ON UP TO 5 PCS &
MACS
>> MOBILE OFFICE APPS
OFFICE APPS FOR TABLET &
SMARTPHONES
>> WINDOWS 10 ENTERPRISE –
PER USER
>> MY ANALYTICS
INDIVIDUAL& TEAM
EFFECTIVENESS

>> EXCHANGE
BUSINESS-CLASS EMAIL &
CALENDAR
>> ONEDRIVE
CLOUD STORAGE AND FILE
SHARING
>> SHAREPOINT
TEAM SITES & INTERNAL
PORTALS
>> SKYPE FOR BUSINESS
ONLINE MEETINGS, IM,
VIDEO CHAT
>> YAMMER
PRIVATE SOCIAL
NETWORKING
>> TEAMS
PERSISTENT
CHAT/VIDEO-BASED
COLLABORATION WITH REACH
COMMUNICATION PLATFORM
>> PLANNER
>> FORMS
>> POWERAPPS

>> ANTI VIRUS
SIGNATURE BASED AV/AS
>> DATA LOSS PREVENTION
PREVENT SENSITIVE DATA LEAKS
>> BASIC EDISCOVERY
DISCOVERY CONTENT ACROSS
EMAIL, DOCS, IM, SOCIAL.
>> AZURE AD PREMIUM P1
SSO, MFA, CONDITIONAL
>> ACCESS, REPORTING
>> INTUNE
MDM, SCCM, ENDPOINT
PROTECTION
>> AZURE INFO PROTECTION
PREMIUM P1
NCRYPT AND TRACK ALL FILES
>> ADV THREAT ANALYTICS
PROTECTION FROM
ADVANCED TARGETED
ATTACKS BY APPLYING USER
AND ENTITY BEHAVIOR
ANALYTICS
>> SECURE SCORE
ASSESSES YOUR CURRENT O365
SECURITY HEALTH
>> COMPLIANCE MANAGER
TRACK COMPLIANCE AGAINST
REGULATORY
REQUIREMENTS

>> DEFENDER FOR O365
ZERO-DAY VIRUS &MALWARE
PROTECTION WITH ATTACK
SIMULATOR
>> ADV THREAT INTELLIGENCE
GLOBAL MACHINE LEARNING BASED
THREAT DETECTIO & PREVENTION;
ENHANCED DATA ACCESS
CONTROLS (CLB)
>> CLOUD APP SECURITY
DISCOVER CLOUD-BASED APPS,
GAIN INSIGHT INTO SHADOW IT AND
ASSESS RISK.
>> AZURE AD PREMIUM P2
RISK BASED CONDITIONAL ACCESS,
PRIVILEGED IDENTITY MANAGEMENT,
IDENTITY PROTECTION
>> DEFENDER FOR IDENTITIES
END USER BEHAVIORAL ANALYSIS
LOOK FOR ABNORMALITIES IN YOUR
ENVIRONMENT
>> DEFENDER FOR ENDPOINT
END-POINT DETECTION &RESPONSE
AGAINST ZERO-DAY MALICIOUS
ATTACKS

>> INFORMATION PROTECTION &
GOVERNANCE
CLOUD DLP (MCAS + ENDPOINT DLP)*
COMMUNICATIONS DLP (TEAMS
CHAT)
INFORMATION PROTECTION
INFORMATION GOVERNANCE
RECORDS MANAGEMENT1*
RULES-BASED AUTO CLASSIFICATION
MACHINE LEARNING-BASED AUTO
CLASSIFICATION1*
CUSTOMER KEY
ADVANCED MESSAGE ENCRYPTION
>> INSIDER RISK MANAGEMENT
COMMUNICATION COMPLIANCE*
INFORMATION BARRIERS
CUSTOMER LOCKBOX
PRIVILEGED ACCESS MANAGEMENT

>> POWER BI PRO
LIVE BUSINESS ANALYTICS
AND VISUALIZATION
>> WORKPLACE
>> ANALYTICS
TEAM AND COMPANY WIDE
EFFECTIVENESS BASED ON
MACHINE LEARNING

>> AUDIO CONFERENCING
WORLDWIDE DIAL-IN FOR
YOUR ONLINE MEETINGS
>> PHONE SYSTEM
BUSINESS PHONE SYSTEM IN
THE CLOUD
WHY Microsoft Cloud
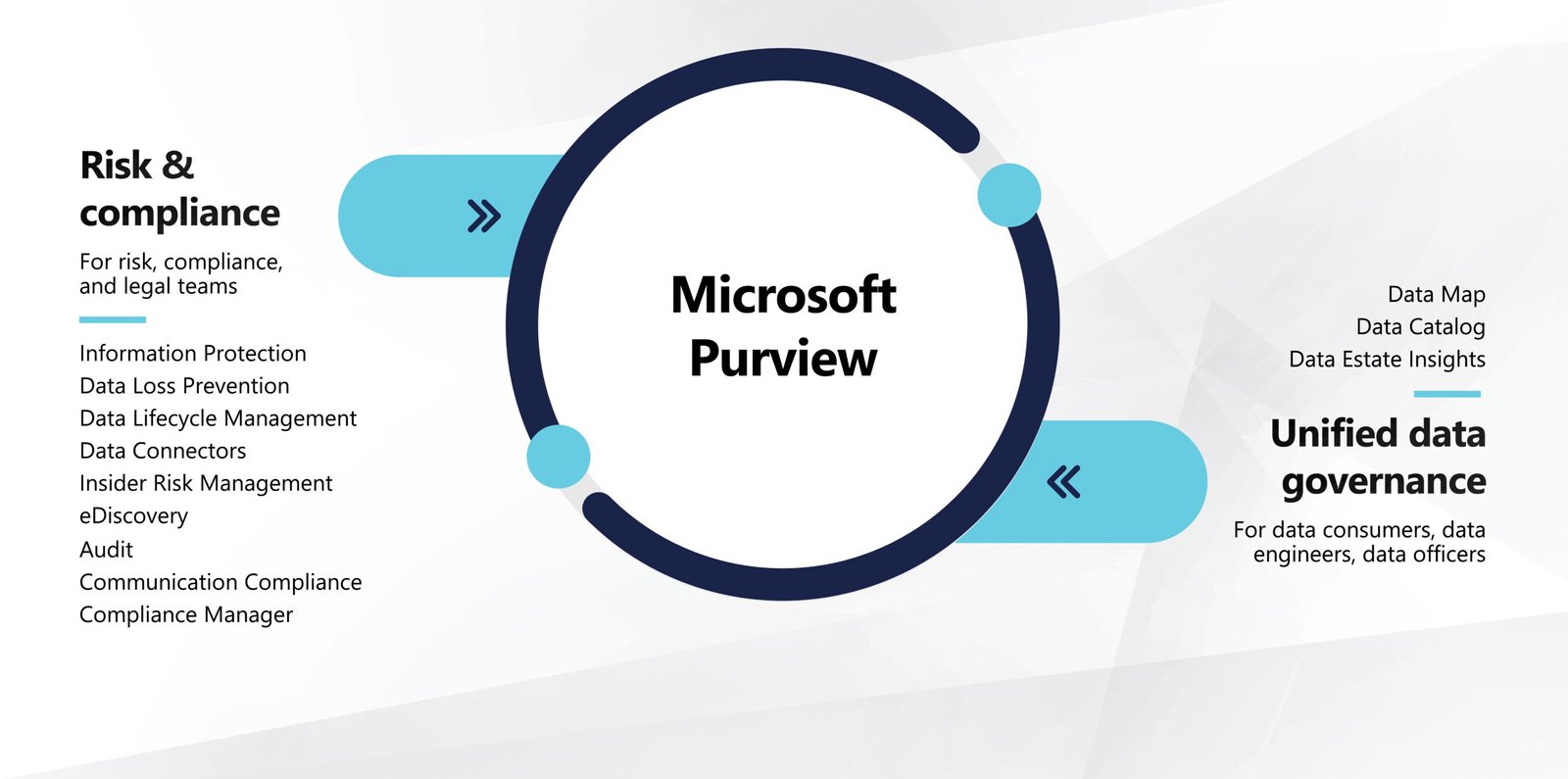
Microsoft Purview Brings Together Solutions From Our Compliance And Data Governance Portfolios
SECURE YOUR ORGANIZATION WITH ZERO TRUST

